A few words about my IOCCC 2015 entry...
The source code of IOCCC 2015 winning entries have been published recently. My source code is here.
Quick start
You can compile prog.c using gcc -o prog prog.c and start playing with the resulting binary (I tested in on Ubuntu and FreeBSD).
It looks like this:
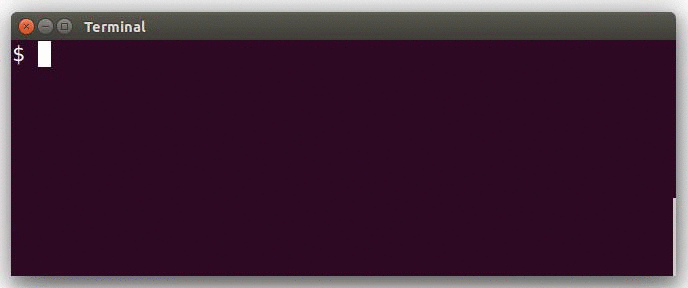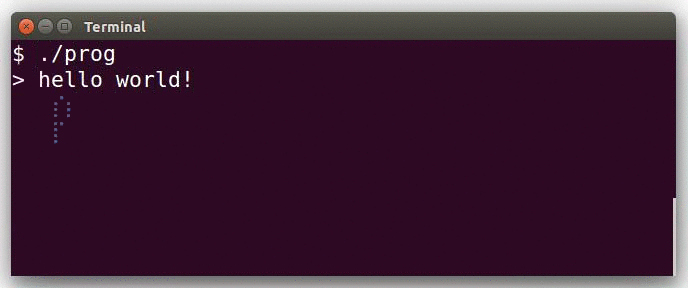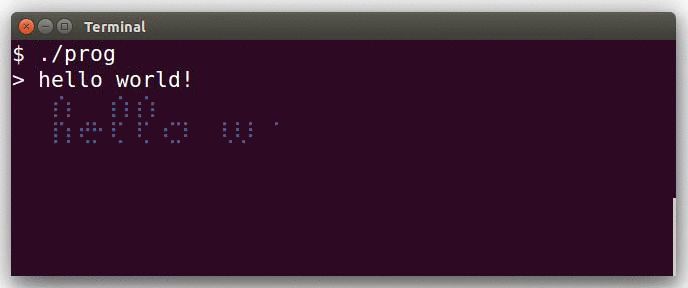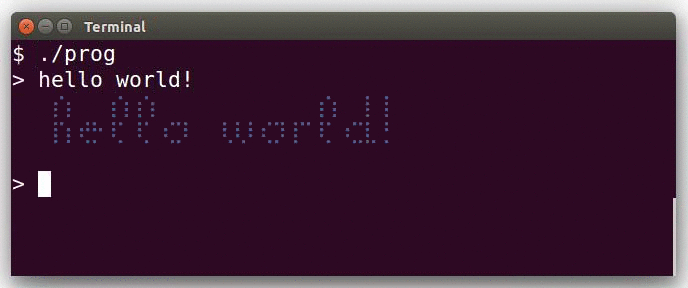
This actually demonstrates the interactive mode.
Alternatively, you may specify the input data (e.g. echo 'hello' | ./prog). In this case no prompt is displayed and the rendering starts immediately.
The program uses the braille patterns range of the unicode standard: this allows to consider each terminal character as a tiny 2x4 bitmap.
Obfuscation
The program is obfuscated in various ways. Let me explain the most unusual one.
At some point, the program swaps file descriptors 0 (usually stdin) and 1 (usually stdout).
This is achieved using dup() and close() function calls.
As a result, functions such as printf(), puts(), write(1, ...) will write to stdin instead of stdout.
Depending on the way you start the program, writing to stdin may succeed or not:
| Command Line | Stdin is… | Writing to stdin will… | |
| (A) | $ ./prog |
current tty (same as stdout) | … succeed! |
| (B) | $ ./prog < file.txt |
file.txt (opened read-only) | … fail. |
| (C) | $ echo test | ./prog |
the pipe (opened read-only) | … fail. |
In the code, the program always tries to print the 2 chars of the interactive prompt, using write(1,"> ",2).
It succeeds in case (A) and fails silently in case (B) or (C).
This is how is handled the interactive vs non-interactive modes. The program actually always acts the same, but a complex side effect of the file descriptors swapping makes it behave differently depending on how you started it.
What’s next?
For more details about secret features or obfuscation aspects you can check out the hints file which compiles judges’ comments and my own explanations.
I also recommend looking at the other winning entries, some of the authors have been very imaginative!
